The Enigma
3-wheel Enigma
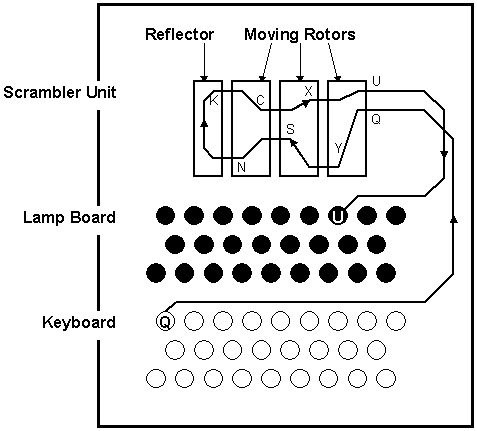
The Enigma was first built in 1923 when it was a commercial product patented by Arthur Scherbius and primarily aimed for businesses. Below is a diagram of the way the 3-wheel enigma works. The concept is quite simple in this model where the key pressed is translated through a series of rotors each mapping a letter from one onto another. The thing that made the enigma better than normal encrypting systems was that each letter typed would turn one or more of the wheels so the encryption key would be constantly changing. As long as the encoder and the decoder had the same keys as the starting position the rotors would move exactly the same and the key would be changing in exactly the same manner. This is a large improvement over the old systems of having every letter being translated into another letter and it would stay that way throughout the message. In the old system an educated guess would lead to the key. The Enigma had three wheels each in 1 of 26 positions. 26 3 = 17576. Although this was a large number the German military added two other features into the enigma to make it harder to crack.
4 wheel Enigma
Because the 3 wheel Enigma would only be able to encode and not decode without heavy rewiring inside the machine a simple addition was made to the machine. A fourth wheel would reflect the signal from one side of the machine to the other. The signal would travel again down the same wheels as it came in but the reflector wheel would not allow a letter to reflect onto itself. So the reflected signal would not meet the one coming in. This caused a tiny glitch in the system and did not allow a letter to be encoded onto it self. But it was believed that the fourth wheel would make the system more secure. This was a very clean way of making the machine an encrypter and a decrypter at the same time as there is a direct connection between the key pressed and the encoded key. So if I pressed Q I would get U and if I pressed U I would get Q as long as the key is the same. This wasn't the only addition that was made.
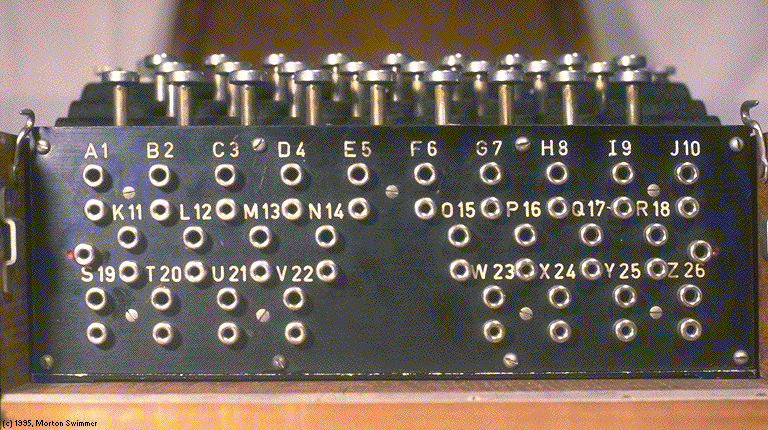
Stecker
The stacker made it possible to directly map keyboard letters onto other letters using the Stecker. The Stecker was simply a plugboard with all the 26 letters. If a wire would be placed between two letters these letters would be swapped. For example a wire between Q and W would mean If I pressed Q the Enigma would treat it as a W and W would be treated as a Q. Unfortunately the swap occurred on both the display and the keyboard. This meant that a letter could still not be encrypted to itself.

German message etiquette
The German messages had a structure of a header followed by the message. The header would have information like the destination time date and most importantly the key that's to be used in the message. The header would be transmitted encrypted in the daily key. The original messages would firstly have the key that is used to encrypt the second key. The second key would be then encrypted with the first key. It would be typed twice so as to make sure it is transmitted correctly. For example:
The 1st key decided on was FRX, so "FRXFRX" was transmitted encrypted in the daily key. The Enigma would be the set to FRX key and the second random key would be typed in. In this case lets say the second key is AGI so "AGIAGI" is typed into the Enigma and the output HCALNU is outputted. This is the transmitted. Then the Enigma is set yet again to AGI and the message can be then encoded.
This was the situation for many years but eventually the German military sent out books of day keys to encode the header. The keys would change daily and so it made the system secure from people who had the Enigma but were not kept supplied with the daily codebooks. This was an obvious move because in time of war some Enigmas can be captured.
In February of 1936, the reflector was introduced into secret correspondence. But, the Germans forgot to change the wiring of the three rotors.
In September 1938 the format of the messages had changed totally to a new more secure type. But still the old format was sometimes used.
This wasn't the last time the coding system changed. In December 1938 2 more rotors were introduced to the existing 3 and so the number of possible rotor positions increased to 60 from 6.
Polish situation
In 1926 the German navy and in 1928 the army codes were no longer decryptable by the Poles. Eventually they discovered that the Germans started to encode their messages using a new code. To counter this Poland set-up the Polish Biuro Szyfrów (Cipher Bureau) and employed three mathematicians: Marian Rejewski, Jerzy Rózycki and Henryk Zygalski.

Catching the Enigma
There are a few versions of how the Poles got hold of the Enigma. The more exciting storey tells that in 1928 the German administration in Warsaw was sent an Enigma by ordinary freight. Realising the danger of it being let out into Polish hands they made urgent enquiries about it. The Polish customs then intercepted the package on suspicion due to the interest by the Germans. The Polish BS4 group (German Cypher Bureau) had 2 days in which to work out how the machine works and repackage it as if nothing happened.
The more probable story which is claimed by the three men who were working on the project is that Hans Thilo-Schmid who was in charge of destroying the used Enigma codes tried to sell a booklet detailing the Enigma to the French and the British. Both countries were not interested as the information was far too small to even attempt an assault against the Enigma. Luckily the French informed Marian Rejewski in Poland of the offer. The Poles accepted enthusiastically. At this point thanks to Hans Thilo-Schmid the Poles had original and encrypted messages and the keys used to encrypt them. They also had the information of how to work the Enigma so the basic workings of the machine could be worked out. They also acquired the commercial version of the 3 wheel enigma. The one thing hat was not known was the rotor wiring.
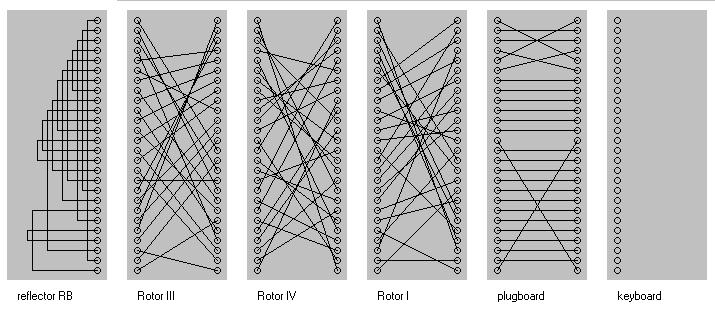
Rotor Wiring
Although the Enigma booklet gave details about the machine but the internal wiring of the rotors were not necessary to operate the machine so they were obviously not included. Rejewski created an equation which linked the four pieces of information: original text, encrypted text, encryption key and finally the rotor wiring. The equation couldn't deal with numbers but rather with permutations. By assuming that only the fast rotor moved, 5 letters were fed into the equation and eventually the fast rotor wiring was calculated. But this system would only work on the fast rotor. Again by luck the strategies used by the Germans to make the Enigma more difficult to crack made it easier. The rotors would be swapped every 3 months and by repeating the process every 3 months all the wiring configurations were found out.
Keyboard connections
Finally the Poles had the three rotors and a commercial version of the enigma to try out. After trying to decrypt one of the messages that they knew the original text to they found they got nonsense. The equations were rechecked but nothing seemed to be wrong. Those were definitely the correct rotor configurations. Until Rejewski though "what if the keyboard isn't wired the same way as the commercial one?" There were '26!' (26 * 25 * 24... * 1) or 4e26 possibilities. The people who made the military version changed the keyboard layout from the original and it could be anything. Everything stopped in its tracks until the Rejewski on the off chance swapped the wiring from the commercial model of being in line with the keyboard so Q=A and W=B etc to alphabetically A=A and B=B. By chance it worked. And the Poles could finally listen to the secret German messages. The year was 1933 and Poland finally had a working Enigma constructed using intelligence.
Key Cracking
To have an Enigma wouldn't give you automatically a way to decrypt the messages because there is still a key to think about. The key would change everyday. All messages would start with a "TO_" or "ANX" in German (X was used as a separator). These were called "Cribs". A crib is a small fragment of text that's known to be there by the listener. When a message is intercepted the first three letters are known to be the encoded versions of "ANX". Thus you can find all the possible starting positions that would create this pattern. Then these can be tried out and see if they make sense. Of cause there are a lot of combinations to try but the job was made easier by the transmitters choosing simple codes like AAA or HIT, LER etc. The job was slow and tiresome.
Double Password Encoding
This was not the only fault in the system. The passwords would be sent out twice and encrypted twice. This meant the crackers would know that the first letter in the key would be the same as the one four letters after it.
ABCABC might encode to WERTYU
There are only a few combinations where a key would change a letter to a W and then three moves on it would change the same letter to a T. This way we can throw out most of the possible keys. Then repeat for EY and RU. If this still leaves possibilities then feed in another message that day as they all use the same code for the header. The problem is we would have to look through all the possibilities to see which ones it would be possible on.
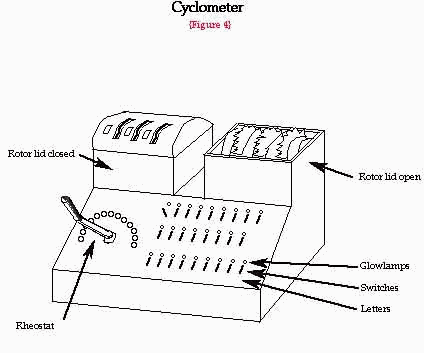
Cyclometre
In 1934 the Polish team invented the "Cyclometre". Operated by hand it took a year to construct a card catalogue of all the 17576 possible combinations. The machine would take each of the letters and for every key it would encrypt it twice with the keys being 3 strokes apart. Once completed it would take 20 minutes to look through it and find the code for that day. All that was necessary was to overlay the sheet with the days information over the sheets created by the Cyclometre. The holes through which the light shone through would indicate a possible solution. In November 1937 again fundamental changes took place in the wiring of the Enigma and the cards had to be remade. After just under a year the cards were remade and just in time for 15th September 1938 when Germany stopped encrypting the keys twice. The Poles were back to square one.
Bomby
A new method was tried which involved a new machine. The method used went back to the use of the Cribs. The Bomba would work its way through every possible setting of the rotors and eventually stop when reaching the right combination. The machines would have three sets of rotors for each of the three letters tested. The tests were usually done on the first three letters of the header as they were assumed to be "TO_". This would have to be done on 6 different machines in order to try all combinations of the rearrangements of the three rotors. The Bomby would tick away until they found the combination. The ticking sound and the suspense is possibly the reason for their name. Unfortunately they were made too late as in December 1938 Germany adder two more rotors and even though only three would be used at a time the combination of rearrangements or rotors jumped from 6 (3!) to 60(5!/2!). The Poles didn't have the time or the money to build them. They were able to apply the Bomby to the task of reading the backlog of messages but they could see that war was just around the corner and Poland was not the best place to conduct these operations.

The meeting with the British
In July 1939 a secret meeting in the Kabackie Woods near the town Pyry the Poles gave their solution to the Enigma problem. The British were amazed by the progress and immediately started to work on their versions of the Bomba. On 1st September 1939 Poland was invaded and the team fled towards France with the fake Enigmas and Bomby. When they got to France they carried on working on decrypting the German codes until the invasion of France. Rejewski eventually made it to Britain but was never allowed to work in Bletchley Park. Even through the period of not knowing the 6th and 7th Rotor combinations and Rajevski having past experience in the field his application was denied. Most of the team were caught by the Germans while fleeing into Spain. Any that survived were not rewarded highly with honours.
Rejewski returned to Poland after the war where he held minor administrative posts at the university in Poznan. Henryk Zygalski remained in England where he taught at Battersea Technical College.